IoT, ENDPOINT AND MOBILE SECURITY – THE EFFECTS OF BYOD ON CYBERSECURITY
Several industries and IT personnel have come to terms with the modern-day approach of Bring Your Own Device (BYOD), as they strive to make operations more and more flexible, efficient and seamless, addressing every possible challenge that could hinder the workflow in any way. Companies are adopting workplace mobility practices amidst the proliferation of modern technology and the increasing number of connected devices that people are using in their day-to-day routine. Permission to use own mobile devices at the workplace and the growing network of IoT devices is leading to the expansion of network with an increasing number of endpoints. It has become imperative for the companies to have befitting cybersecurity policies and a robust endpoint security solution that best suits their work model and ensures a safe haven for the business-critical processes and data.
But before defining cybersecurity policies around BYOD and mobile devices and IoT devices, one should be clear with the distinctions between mobile device management and endpoint security. They should profile the IoT and mobile devices to understand the different operating systems they use, the functions they are capable of performing and the actual utility of them for the business. This will help in defining policies that can effectively control the use of such devices at the workplace as well as outside the work premises for work purposes.
As per a report by Crystal Market Research, the global BYOD market is expected to grow at a CAGR of 15.38% between 2012 and 2022 and reach USD 318.41 billion in 2022.[1] This trend, often labelled as IT consumerisation, is here to stay, as more and more companies adopt BYOD model, allowing employees to carry their own devices and connect them with the organisational network to access important business data and applications for work purposes.
While BYOD is increasingly touted as an excellent business model, well suited for improving workplace flexibility and productivity; however, it has a significant impact on the IT structure of an enterprise.
Some of the major impacts of BYOD on a company’s cybersecurity setup are as follows:
Expands IT infrastructure
More and more owned portable devices like laptops, tablets and smartphones brought by employees to offices significantly expand the network as they serve as new endpoints to the network. These personal devices have to be connected to the company’s IT infrastructure for which the IT team has to identify the employees’ mobile devices that they’ll be using to access the corporate data and then make necessary adjustments to the company’s IT setup to accommodate them.
Companies are also required to audit these devices to ensure that they align with the company’s security stipulations and device policies, and all this work increases the IT management costs of the company.
Increased risk of data leakage
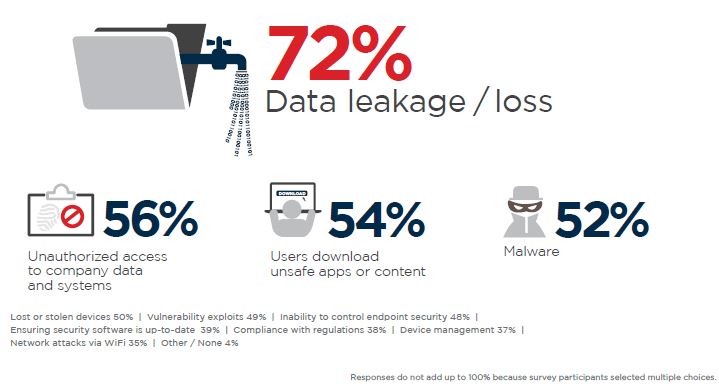
More and more personal devices used for work purposes increase the number of endpoints on the company’s IT network. Presence of multiple endpoints makes it difficult to monitor the activities on each device and tackle malicious programmes or users that try to gain unauthorised access to such devices and thereby the IT infrastructure. This escalates the threat of cybersecurity breach and data leakage.
Mobile devices are considered the weakest link to a company’s security framework. They need to be constantly updated with the latest security patch to cover any type of loopholes and stay protected from any type of malware or virus attack or any unauthorised access. Employees are as much responsible for ensuring the security of their own mobile devices and should see to it that their devices are password protected and updated with the latest software and security patches. The employees and companies are both responsible for reviewing a mobile device’s compliance with the security protocols.
Mixes personal data and corporate data
Devices carried as part of the BYOD model have both corporate and personal data, which makes the loss or theft of such devices a riskier affair.
Companies should take the initiative to back up the essential corporate data present on the device in order to retrieve the data in case of a technical glitch, cybersecurity breach or theft or loss of the device.
Companies can encourage containerisation, which helps in isolating business content in its own workspace thereby keeping the business information secure while still allowing the employees to use their devices for personal as well as work purposes. The approach also helps the company to safely remove the business-related information from the user’s device when the employee exits the company.
Exposes vulnerabilities
Personal mobile devices bring security risks along with them as they reduce a
corporation’s control over data. As the employees use these devices for personal purposes, they tend to download data –sometimes rogue or malicious in nature- or access certain unsecured third-party applications or connect to public Wi-Fi spots thereby exposing the device to considerable security threats.
These devices can carry corrupt/malicious programmes and once the device is connected to a corporate network, the malicious programme can spread to the company’s network of systems if there are inadequate intrusion detection or endpoint security systems. Such vulnerabilities can cause serious data compromise and obstruct the natural course of the workflow.
Increases infiltration of malware
If an employee installs malware unknowingly and connects the device to the organisation’s network, the malware can easily infiltrate the network. Now the likelihood of such an easy mistake is high, with users accessing a disparate range of websites and apps on their personal devices for various tasks. Once a mobile device is corrupted by a malicious file, it won’t take long for the rogue programme to spread across and this can cause serious damage if the attack remains unchecked.
Companies should deploy robust intrusion detection and endpoint security systems and update anti-malware, anti-virus and security patches regularly across the organisation’s IT network and systems connected to it.
In the third quarter of 2017, McAfee Labs identified more than 16 million mobile malware infestations, indicating almost two-fold increase on a year-on-year basis.
Meanwhile, an increasing number of organisations are accommodating IoT devices into their networks in the form of smart devices like smart electronic locks, smart lights, smart thermostats and even connected coffee makers. These innocent-looking smart devices can convolute the endpoint network of an organisation, exposing the vulnerabilities of a corporate’s security defence framework. These IoT devices are connected to a company’s IT infrastructure but rarely have enough security programmes built-in within them to offer protection against any breach or unauthorised manipulations. This way, they are easily discoverable on the internet and offer hackers with easy access points to a company’s IT infrastructure.
In an interesting case, a simple, Internet-connected fish tank was used by hackers to funnel out data from a North American casino. The fish tank’s sensors were connected to a computer system that regulated the tank’s cleanliness, food and temperature. They used this fish tank, which was not secured adequately, as a gateway to enter the casino’s network, as the tank was connected to the same network as the computers and other systems of the casino. The hackers managed to move into other parts of the network and sent 10 GB of data to a device in Finland.
This is just one case among several other IoT breaches and exposes the security risks associated with IoT devices.
According to a study by digital security company Gemalto, only 48% of businesses are capable of detecting if any of their IoT devices have been breached.[2] This is alarming, considering the fact that the number of connected devices is set to reach 75.44 billion by 2025.[3]
To tackle such security threats, companies should lay clear rules and policies regarding which devices could and could not be connected to office networks. IoT devices with inadequate easy-to-patch firmware and update schedules should not be allowed to be connected to the corporate network at all, while employees, who are one of the critical attack vectors, should be encouraged to follow all the data and cybersecurity rules.
It is essential for the companies to have proper device management protocols and endpoint security systems as the workplace network gets more complicated with the addition of BYOD and IoT devices.
References:



No comments:
Post a Comment