Admin "Kunal Vohra"
In the era of Government surveillance, ensuring the security and safety of our private communications regardless of platform – email, VOIP, message, even cookies stored – should be the top priority of the Internet industry. Some industry came together to offer Encryption as the protection against government surveillance, but some left security holes that may expose your personal data.
A critical issue on Instagram’s Android Application has been disclosed by a security researcher that could allow an attacker to hijack users’ account and successfully access private photos, delete victim's photos, edit comments and also post new images.
Instagram, acquired by Facebook in April 2012 for approximately US$1 billion, is an online mobile photo-sharing, video-sharing and social networking service that enables its users to take pictures and videos, apply digital filters, and share them on a variety of social networking services, such as Facebook, Twitter, Tumblr and Flickr.
USING UNENCRYPTED HTTPS CONNECTION
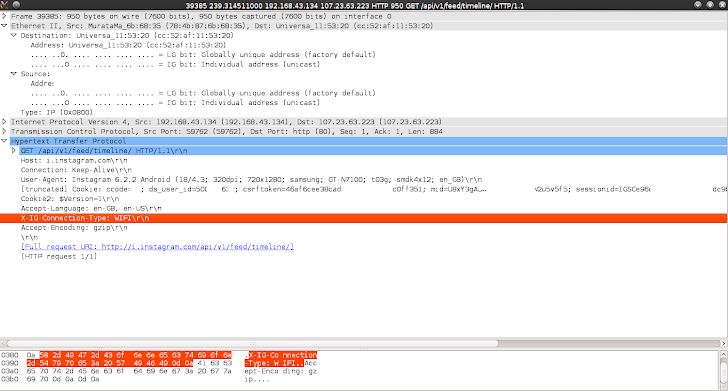
Instagram’s Android Application communicates with its server over an unencrypted HTTP connection, which is susceptible to tampering by anyone in a position to intercept it, Mazin Ahmed, who discovered the vulnerability explained in a blog post.
“I started using the app on my phone, and monitoring the traffic in the network using WireShark, looking for evidence for unencrypted data that goes through the network or a technique to make this data unencrypted (if it was encrypted),” said Mazin.
INSTAGRAM SESSION HIJACKING
He found that the unencrypted Instagram app communication also vulnerable to session hijacking flaw that can be done using a man-in-the-middle attack, common technique used by attackers to intercept wireless data traffic.
Reusing intercepted HTTP session cookies on another system/browser allows the attacker to hijack the session of the victim's Instagram account.
“As soon as I logged into my account on my phone, Wireshark has captured unencrypted data that goes through HTTP. This data includes: The pictures that the victims watching, The victim's session cookies, the victim's username and ID.”
It is really surprising that the largest social networking giant Facebook ignored such a big issue in its most popular image and video sharing service and failed to take the maximum measure to insure the security of its users.
Mazin, who believes the issue might be getting exploited by the intelligence agencies for the purpose of surveillance, reported the vulnerability to the Facebook on 24th July, but its security team replied: “Facebook accepts the risk of parts of Instagram communicating over HTTP not over HTTPS.”
Facebook has decided to adopt complete HTTPS for its Instagram mobile application in near future but till now it is not clear that how much time it will take.

No comments:
Post a Comment