Danor Cohen, a Security researcher who recently discovered the 'WinRAR file spoofing vulnerability', has discovered one more zero day vulnerability. This time it is Buffer Overflow vulnerability in one of the popular web application vulnerability scanner 'Acunetix'.
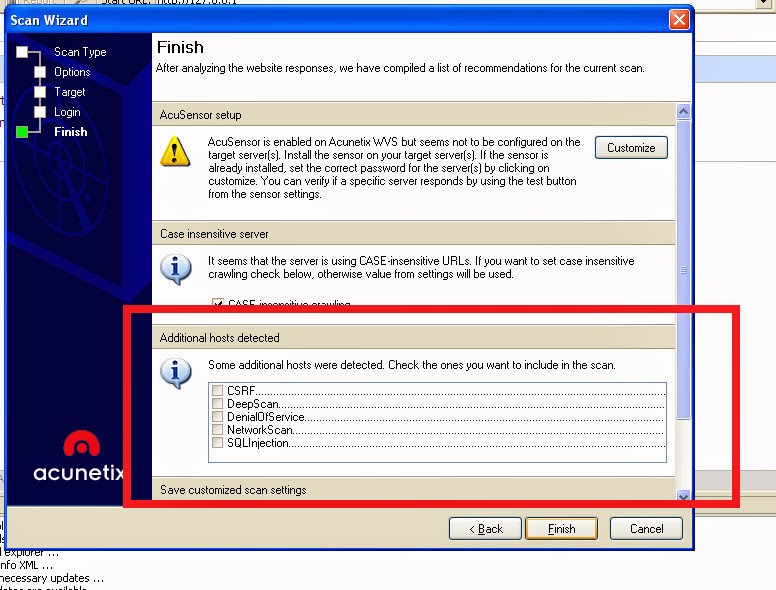
There is a feature in Acunetix that allows to scan the additional domains or subdomains detected during the scan.
"It learns about the external related domains from the external sources that appear at the scanned website, for example: "<a href=http://externalSource.com/ ></a>"
Danor found that if the 'external' source url's length is larger than 268Bytes, the Acunetix vulnerability scanner will get crashed.
Researcher managed to exploit this vulnerability and successfully launched an executable file(calc.exe). By modifiying the code, one can infect the computers of newbies with a malware who attempt to scan their websites.
More technical details are available at his blog post.
There is a feature in Acunetix that allows to scan the additional domains or subdomains detected during the scan.
"It learns about the external related domains from the external sources that appear at the scanned website, for example: "<a href=http://externalSource.com/ ></a>"
Danor found that if the 'external' source url's length is larger than 268Bytes, the Acunetix vulnerability scanner will get crashed.
For Ex:
<A href= “http://AAAAAAAAAAAAAAAAAAAAAAAAAA...........AAAAA”>Researcher managed to exploit this vulnerability and successfully launched an executable file(calc.exe). By modifiying the code, one can infect the computers of newbies with a malware who attempt to scan their websites.
More technical details are available at his blog post.
No comments:
Post a Comment